...
For reference, the kerberods binary I found had signatures:
| sha1 | 9a6ae3e9bca3e5c24961abf337bc839048d094ed |
| md5 | b39d9cbe6c63d7a621469bf13f3ea466 |
Application-level vulnerabilities
...
- Check the audit log for suspicious admin activity, but be aware that the audit log is not trustable at this point.
Identify accounts whose password has recently changed, by comparing password hashes with that from a recent backup.
This command compares thecwd_usertable from a monthly backup to that from the currentconfluencedatabase:Code Block # vim -d <(pg_restore -t cwd_user --data-only /var/atlassian/application-data/confluence/backups/monthly.0/database/confluence) \ <(sudo -u postgres PGDATABASE=confluence pg_dump -t cwd_user --data-only)(diffing database dumps like this is a generally useful technique, described here)
Check for users logging in from strange IPs, e.g. foreign countries or VPSes.
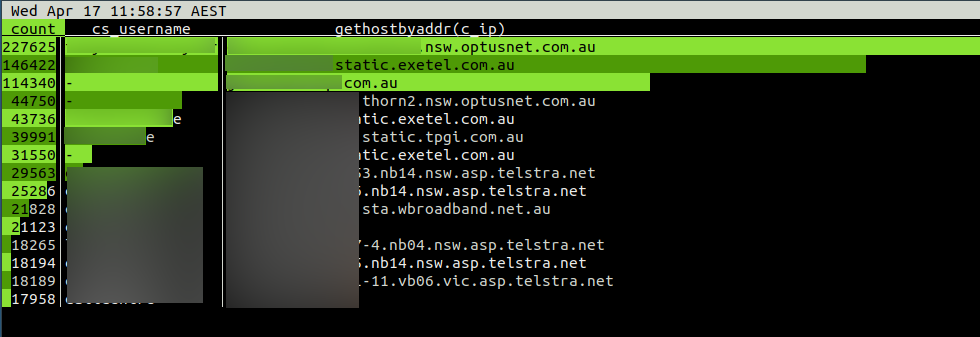
This lnav command prints a summary of Confluence access counts grouped by username and originating IP hostnameCode Block jturner@jturner-desktop:~/redradishtech.com.au/clients/$client/hack$ lnav var/log/apache2/confluence.$client.com.au/access.log* -c ";select count, cs_username, gethostbyaddr(c_ip) from (select distinct cs_username, c_ip, count(*) AS count from access_log group by 1,2 order by 3 desc limit 15) x;"
The originating IPs do not look suspicious for a small Australian business:
...